Blogs.

A case of ransomware, resolved
...

How we discovered outdated Windows Servers
Introduction Managing servers is the process of taking care of computer systems...

The story of a real vishing attack: detailed incident walkthrough
Introduction In this article, we'll cover the following: Context on vishing...
Microsoft Teams Phishing: How to Stop The Rising Phishing Threat
Introduction Around mid-September, our Security Operations Centre (SOC)...

Mitigating Cyber Threats with Risk Intelligence
What is Risk Intelligence - and how can it help you? Business leaders...


Hunting for You and Eye #1
Eye Security's ongoing hunt for cyber threats provides valuable insights into...

Security Alert: Critical Geoserver Vulnerabilities
We want to bring your attention to a critical vulnerability in GeoServer that...

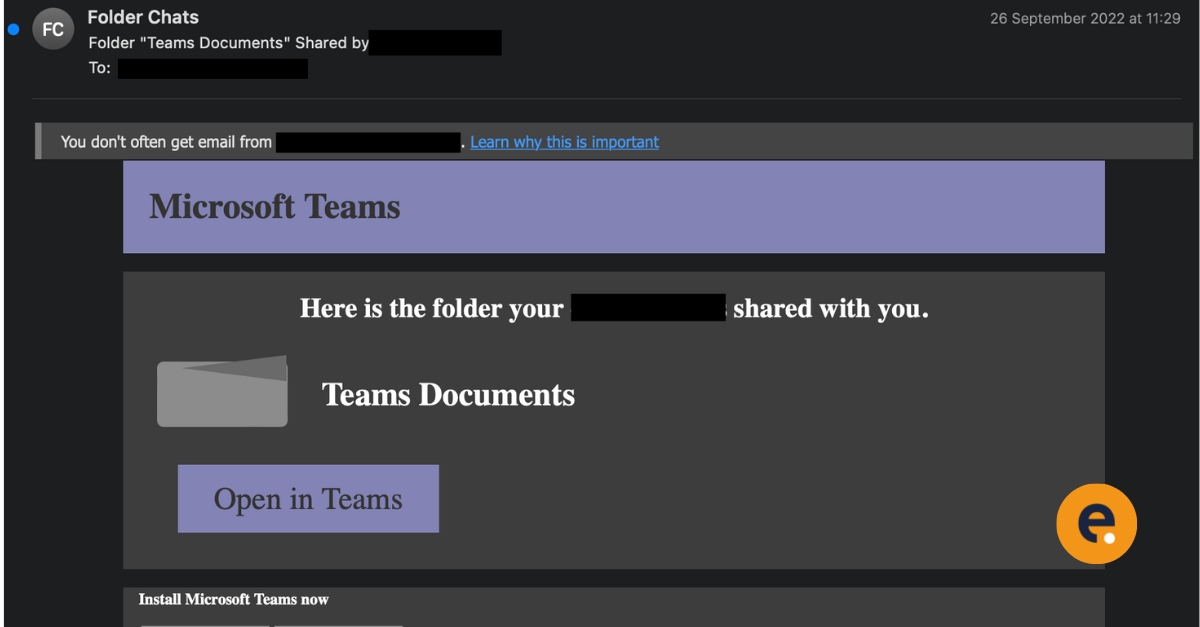
Large scale phishing campaign quickly utilises Legacy Authentication before Microsoft disables it
Security Specialists from Eye Security have observed a rather large phishing...

WinRS and Exchange, a sneaky backdoor
How it started ? On the 10th of May around lunch, our Security Operation Centre...

Are new employees the weakest link in your organisation?
We have all been there: starting a new job can be very overwhelming. There are...

