Blogs.
How Microsoft might have lured unsuspecting end-users into the hands of criminals
...


Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...

8Base Ransomware Recovery: Key and File Retrieval
The Eye Security Incident Response team was recently engaged to investigate a...


This Is How Threat Actors Use OneDrive Compromise to Infect Local Windows Hosts
The trusted status of Microsoft cloud applications has inevitably resulted in...

Business Email Compromise: Fifteen Steps to Reduce the Risk
Business email compromise (BEC) is a concept that first appeared around 2013...

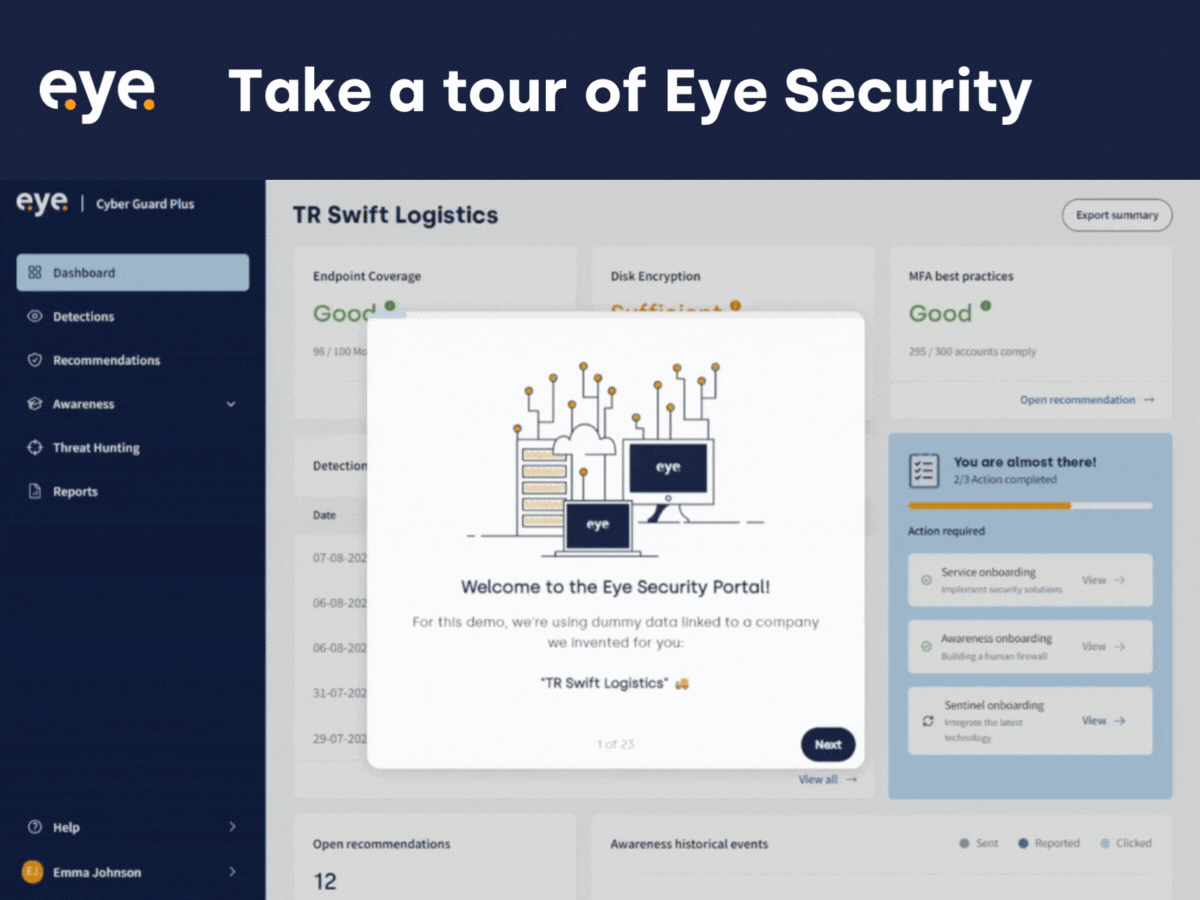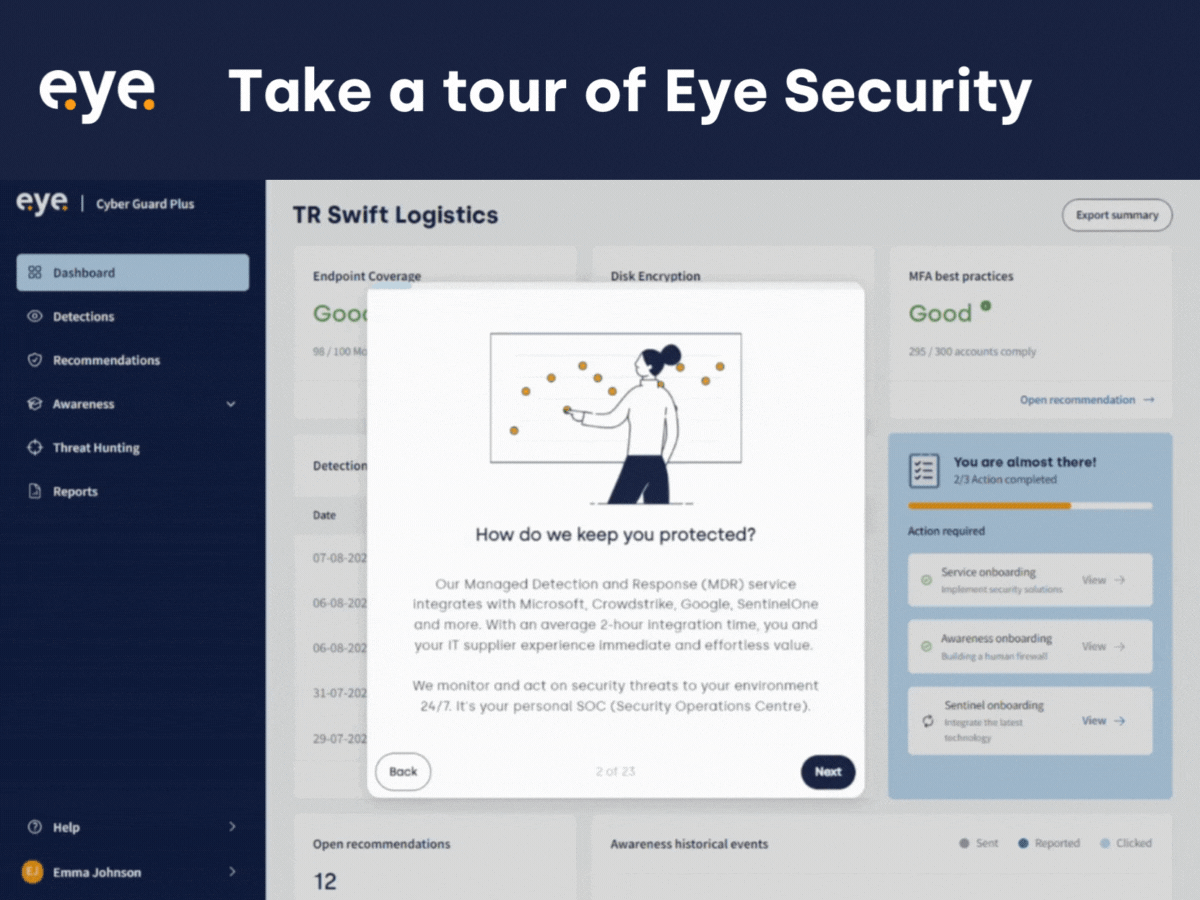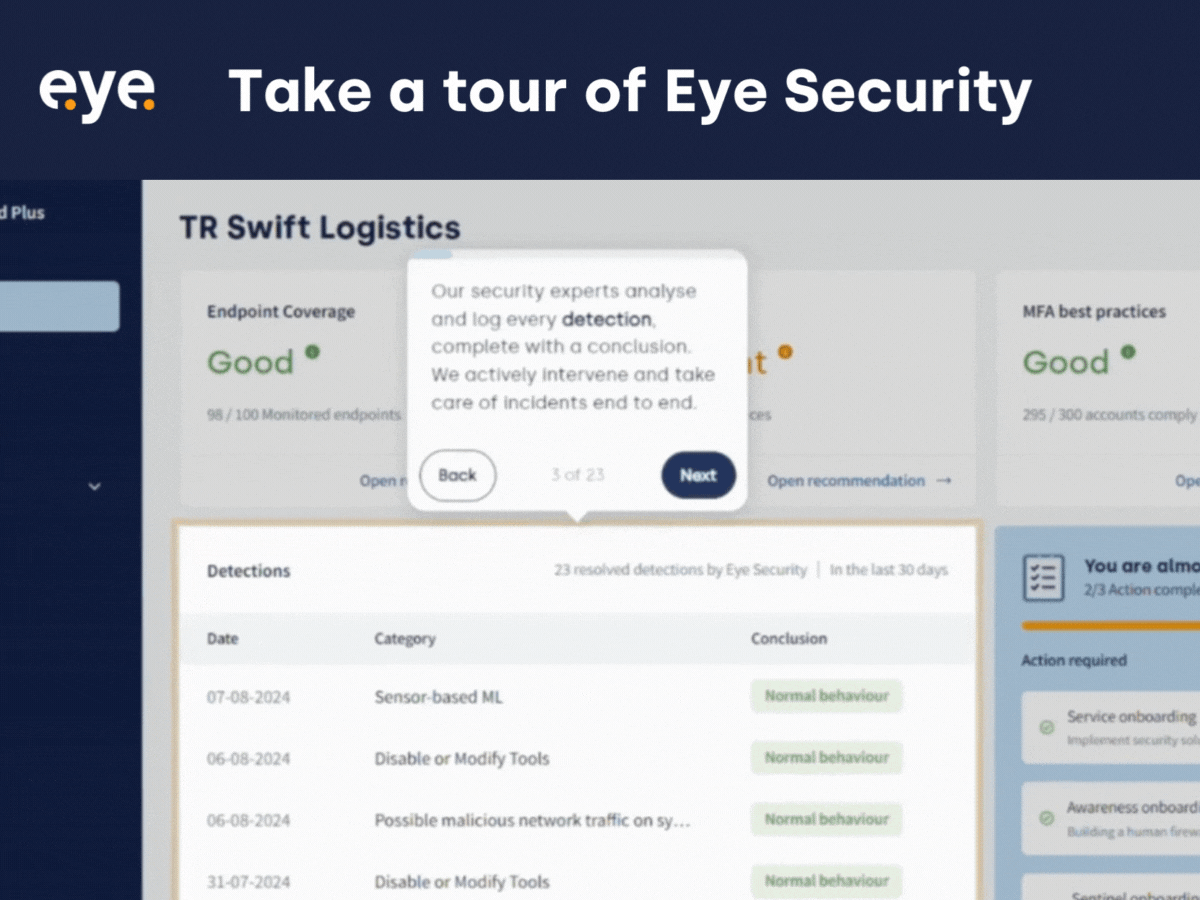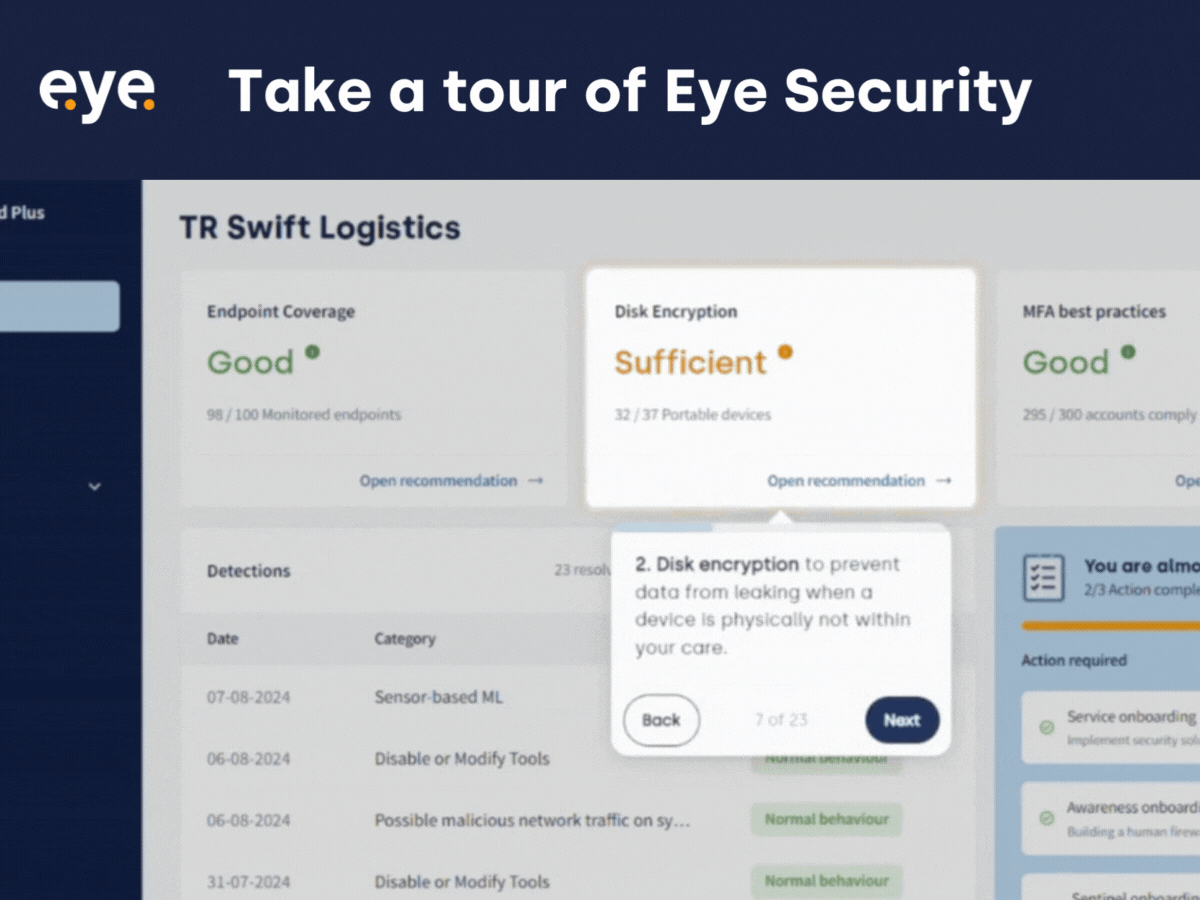
Product Update: Demo Portal
In this blog, we sit down with Anne Postma, our Product Manager, to discuss the...

Product Update: Vulnerability & Threat Hunting
In this blog, we interview Robbin Begeer, Product Manager at Eye Security,...
CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...

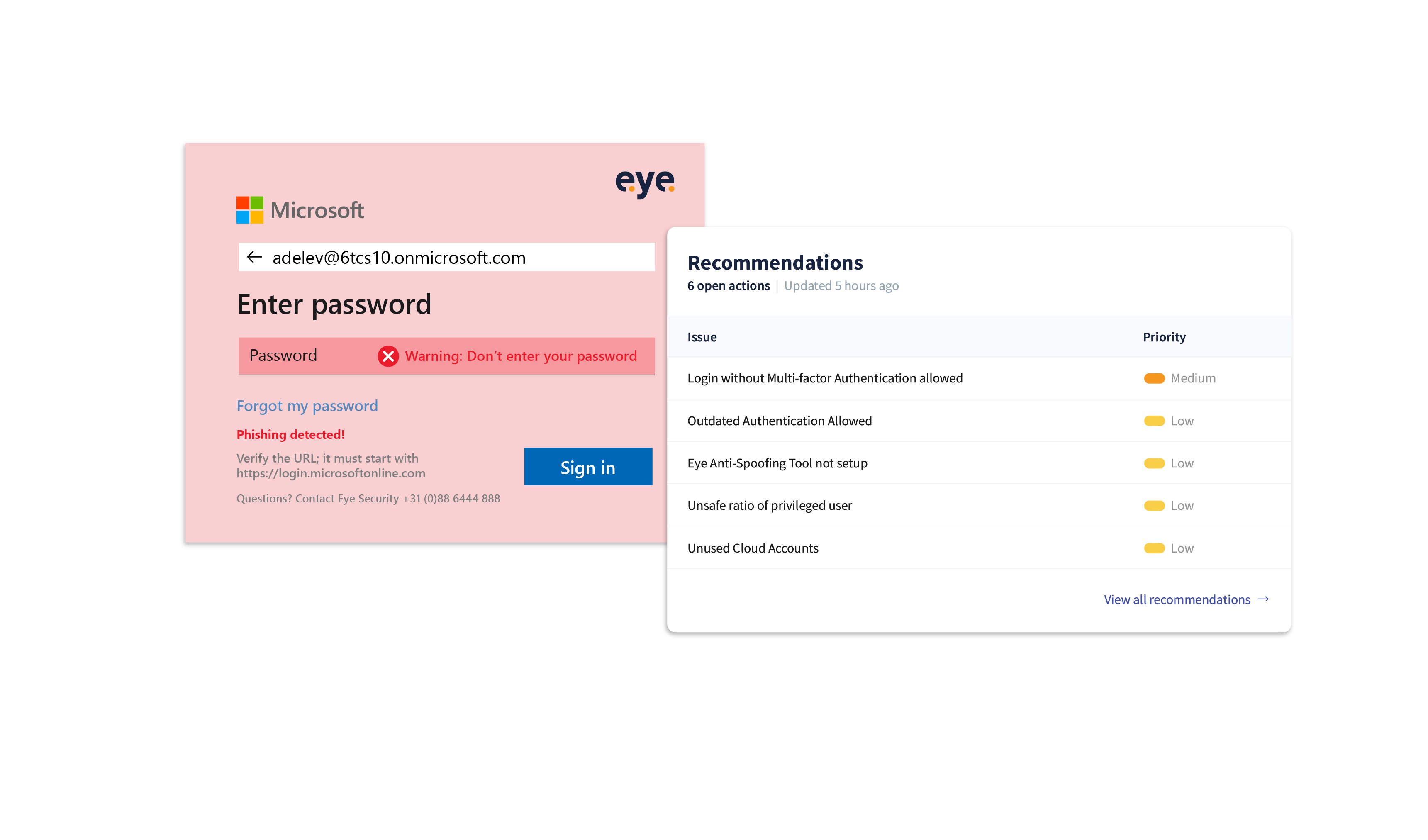
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...

How Microsoft might have lured unsuspecting end-users into the hands of criminals
...

A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...