Blogs.
How Microsoft might have lured unsuspecting end-users into the hands of criminals
...


Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...

CrowdStrike Falcon and Microsoft blue screen issue updates
Last updated: July 30th at 00:00 CEST In this blog, we provided real-time...

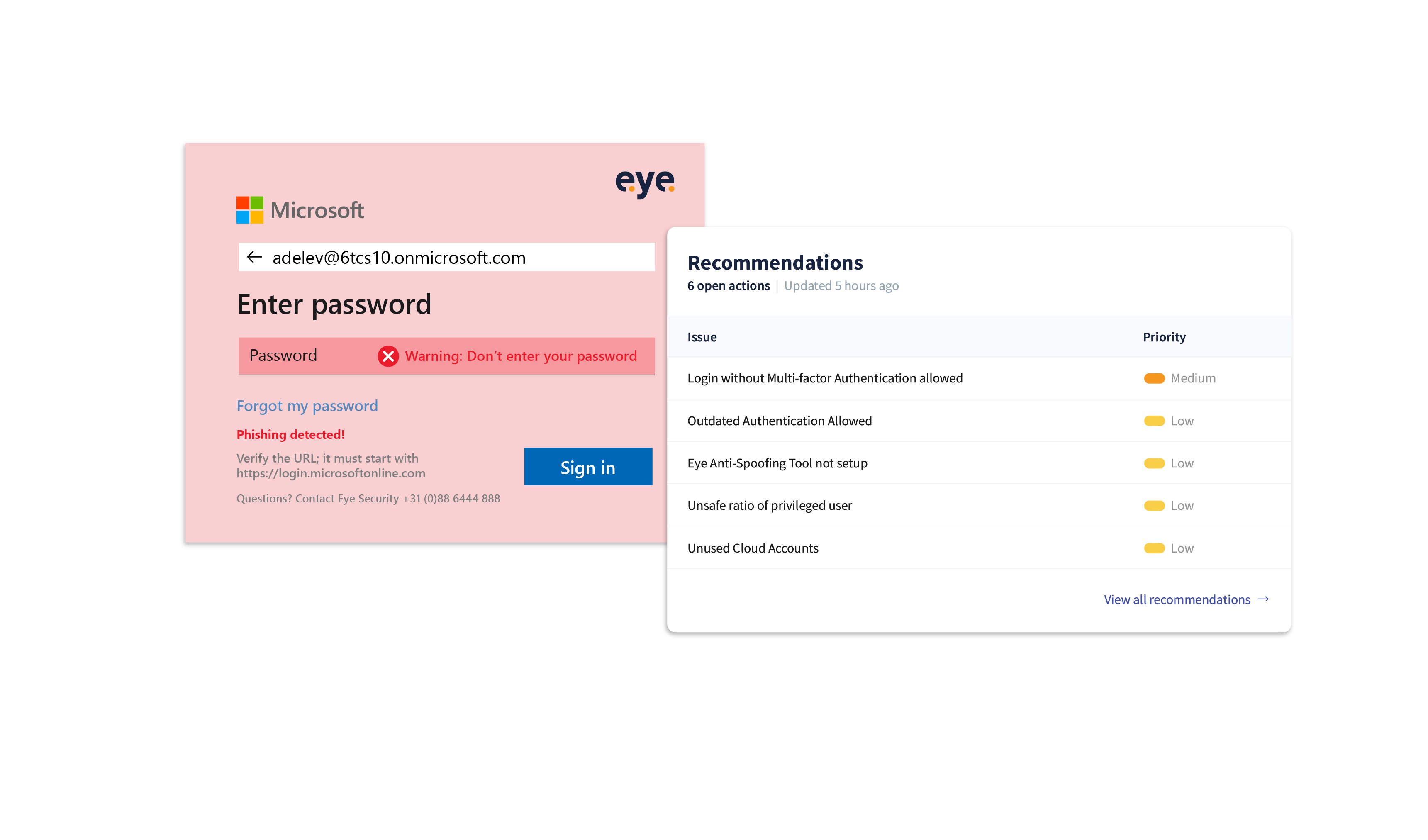
Empowering security: the battle against Login Spoofing
Introduction Battling cyber-crime can sometimes feel like an endless tennis...
“Master” Malware - a new C2 framework
Introduction Recently, during an incident response engagement, we came across a...


How Microsoft might have lured unsuspecting end-users into the hands of criminals
...

A Conti-nuous issue
Introduction In this blog, we shed light on our findings during a forensic...

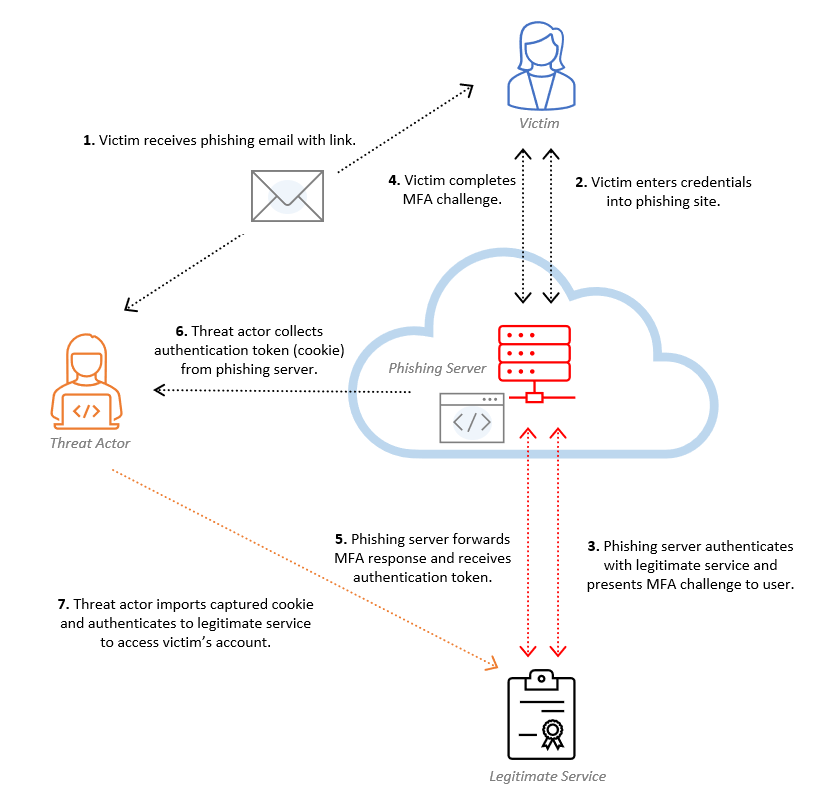
How to defend against EvilProxy when a phishing attack strikes
Here at Eye Security, we have observed a disturbing increase in security...


How we discovered outdated Windows Servers
Introduction Managing servers is the process of taking care of computer systems...

The story of a real vishing attack: detailed incident walkthrough
Introduction In this article, we'll cover the following: Context on vishing...

Mitigating Cyber Threats with Risk Intelligence
What is Risk Intelligence - and how can it help you? Business leaders...