Blogs.
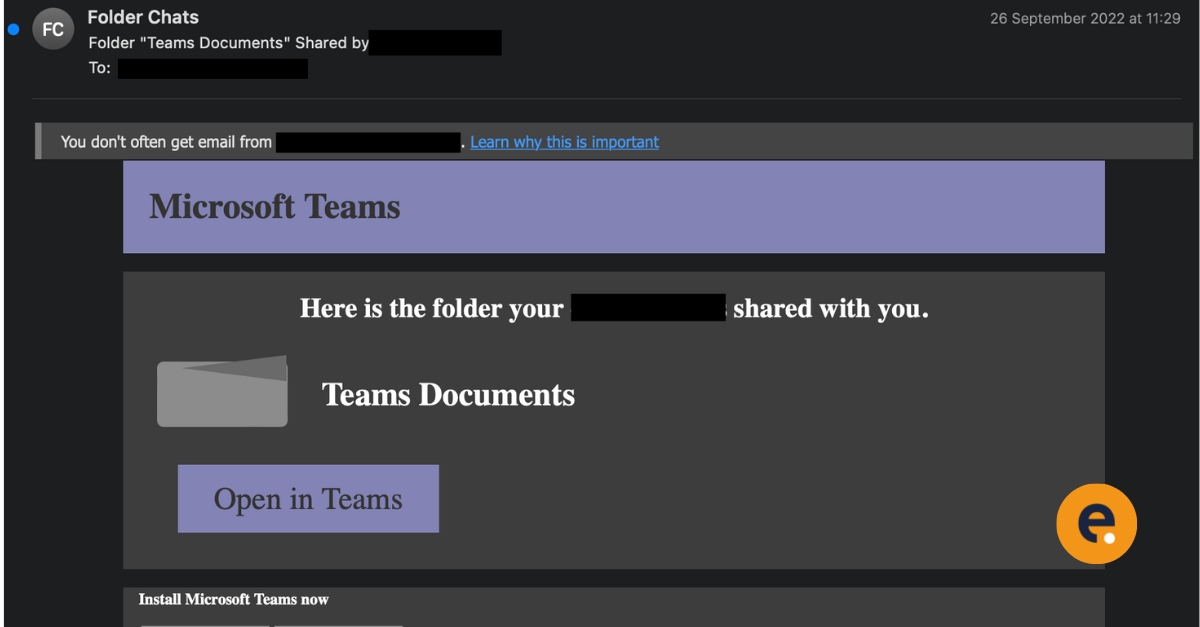
Large scale phishing campaign quickly utilises Legacy Authentication before Microsoft disables it
Security Specialists from Eye Security have observed a rather large phishing...

WinRS and Exchange, a sneaky backdoor
How it started ? On the 10th of May around lunch, our Security Operation Centre...

Are new employees the weakest link in your organisation?
We have all been there: starting a new job can be very overwhelming. There are...

Log4j Critical Updates by Eye CERT
Introduction Attackers are actively exploiting a remote code execution...

5 tips to secure your company for free
No matter how big or small your company is, everyone has crown jewels: crucial...

How does machine learning in cybersecurity help detect threats?
Machine learning makes an important contribution to cybersecurity by...

What is social engineering and how do I protect my company against it?
Social engineering is the temptation of people to reveal sensitive information...

What is a Zero Day? How to Ensure Zero Day Protection for Your Company
A zero day is an unresolved vulnerability in software that puts end users at...

You can protect yourself against supply chain ransomware – here's how
Still in shock, the media is suggesting that there is little that can be done...

Who is responsible for the damage in a cyber attack?
In 2021, the Central Netherlands court made a striking decision. Bol.com and...
