Blogs.
Retail Giants Breached: What the M&S, Harrods & UNFI Attacks Mean for Your Cyber Defences
A surge of high-impact cyberattacks is shaking the retail sector, exposing...
The Eyes Behind Eye Security: Why People Matter in Cyber Security
A message from Piet Kerkhofs, CTO & founder of Eye Security...


Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...


Top 5 Cyber Threats Manufacturers Face in 2025
Cyber attacks can be devastating to manufacturers. They disrupt supply chains,...
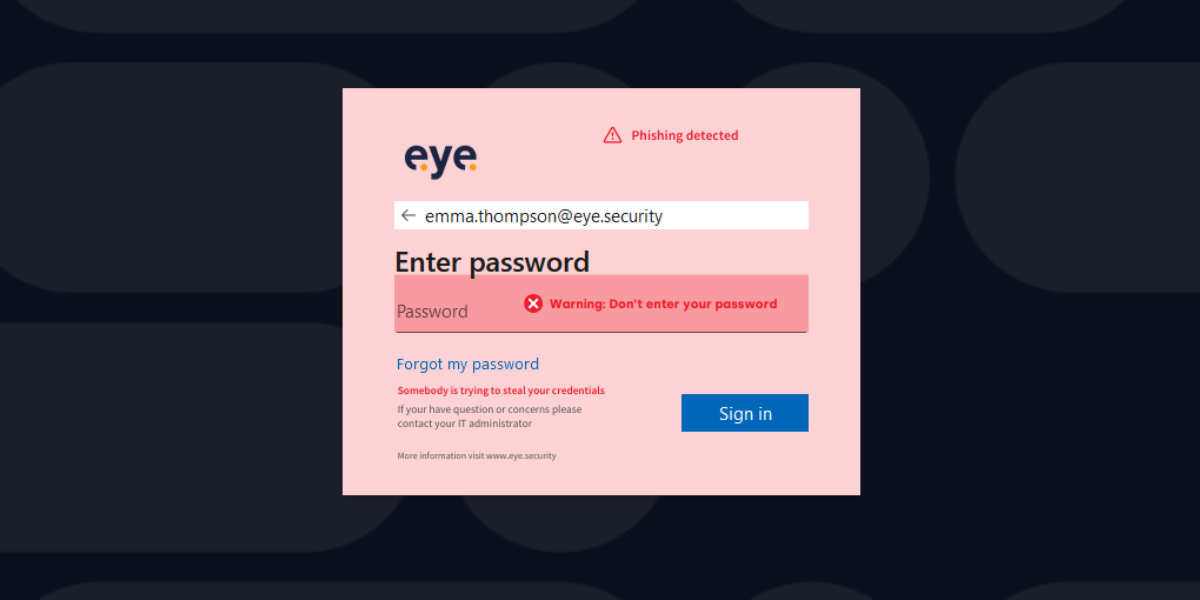
Microsoft 365 Credential Theft? Here’s a Free Anti-Phishing to Bolster Your Defences
Credential phishing is a constant threat. And Microsoft 365? Prime target. It's...
Manufacturing and Cybersecurity: What Are the Challenges?
Manufacturing companies form the very foundation of the global economy....

EDR vs NDR: Why Endpoint Security Has a Clear Advantage
Choosing the right cybersecurity tools can be challenging in a crowded...
Investigation of an 8Base Ransomware Attack Uncovers Surprising Insights
Almost every engagement of the Eye Security Incident Response team provides new...

Business Email Compromise: Fifteen Steps to Reduce the Risk
Business email compromise (BEC) is a concept that first appeared around 2013...

A new paradigm to extinguish cyber risk for good: 24/7 protection connects with cyber insurance
...
