Blogs.

Battling Shadow AI: A Practical Tool for CISOs
Generative AI is transforming how businesses operate. Tools such as ChatGPT,...


Top Cyber Threats in Logistics and How to Defend Against Them
For decades, transport and logistics operators have focused primarily on...
When Business Email Compromise Nearly Costs a Million: An Incident Response Story
Business Email Compromise (BEC) remains one of the most damaging yet...

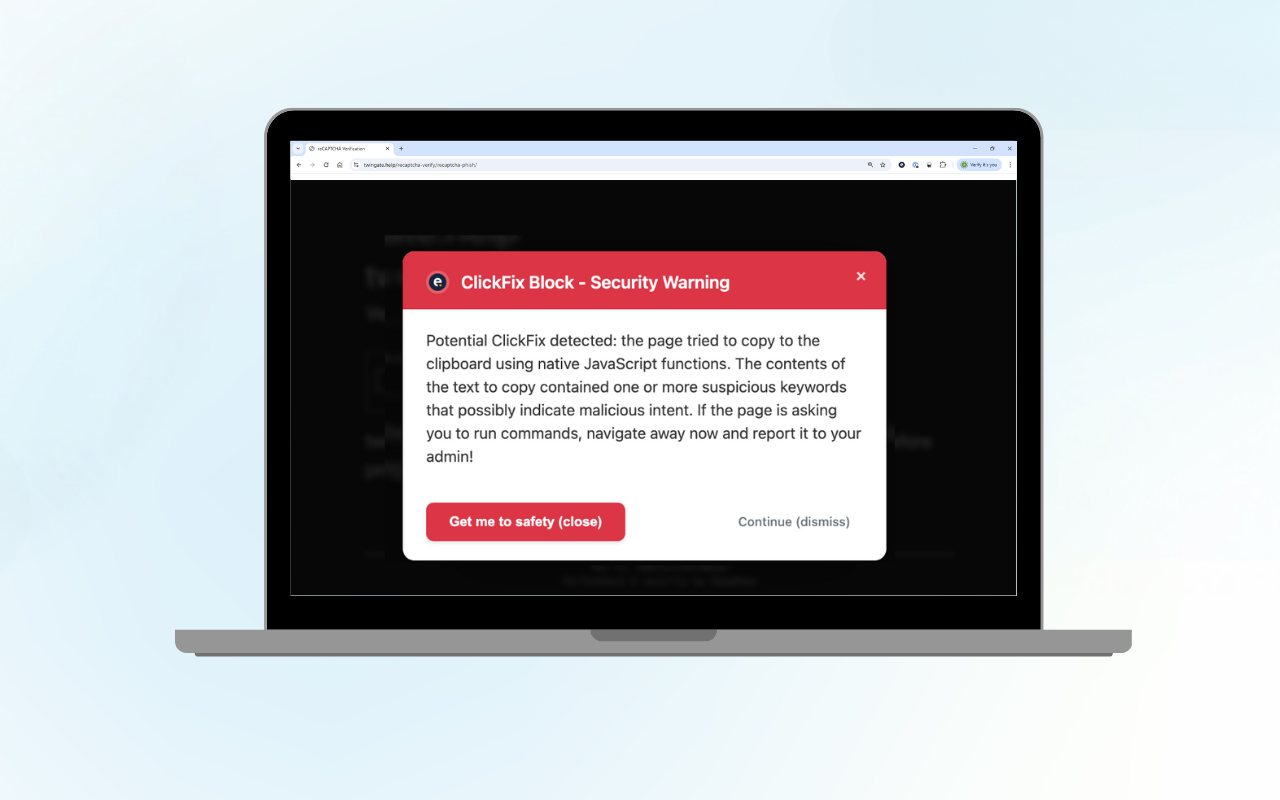
ClickFix Block: Protect Your Organisation from Fake CAPTCHA Attacks
Curious about the technical details? Read our technical blog on ClickFix Block....

Uses of AI in Enterprise Cybersecurity: Risks, Opportunities, Strategies
To fully unlock the potential of AI systems in cybersecurity, organisations...

Dual-use AI in Cyberattacks: How LLMs Are Reshaping the Threat Landscape
The malicious use of AI is evolving, making attacker tactics increasingly...

Hours from shutdown: How a Logistics company escaped ransomware just in time
This is a real incident Eye Security investigated at Move Intermodal. The...

Cybersecurity in transportation and logistics: inside the sector’s risks
Over the past five years, cybersecurity incidents have risen 48%, with the...

Eye Security Uncovers Actively Exploited Zero-Day in Microsoft SharePoint (CVE-2025-53770)
On the evening of July 18, 2025, Eye Security identified active, large-scale...
Brute Force Attack on SSLVPN Leads to Stealthy Network Intrusion
Attacks do not always start with malware or flashy exploits. Sometimes, all it...
