Blogs.
How Microsoft might have lured unsuspecting end-users into the hands of criminals
...

The Eyes Behind Eye Security: Why People Matter in Cyber Security
A message from Piet Kerkhofs, CTO & founder of Eye Security...


$750K Ransomware Attack: Manufacturer's Recovery with Eye Security
Picture this: a state-of-the-art production floor plunges into chaos. Machines...

Sneaky 2FA: Use This KQL Query to Stay Ahead of the Emerging Threat
At Eye Security, we constantly seek out new threats and detection methods to...

8Base Ransomware Recovery: Key and File Retrieval
The Eye Security Incident Response team was recently engaged to investigate a...


Top 5 Cyber Threats Manufacturers Face in 2025
Cyber attacks can be devastating to manufacturers. They disrupt supply chains,...
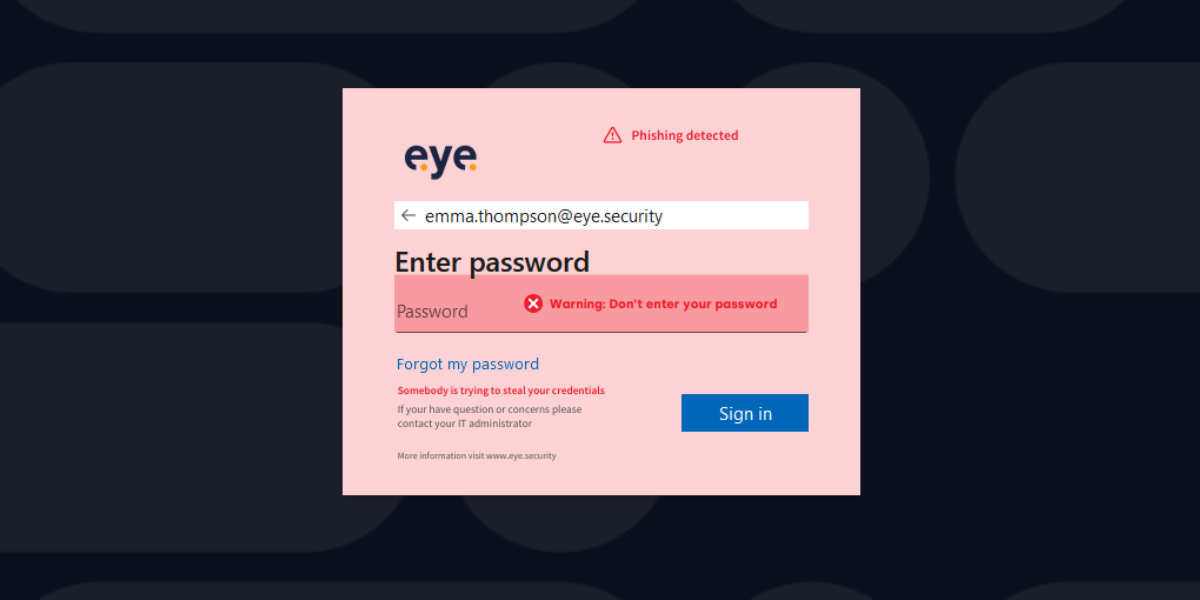
Microsoft 365 Credential Theft? Here’s a Free Anti-Phishing to Bolster Your Defences
Credential phishing is a constant threat. And Microsoft 365? Prime target. It's...
Manufacturing and Cybersecurity: What Are the Challenges?
Manufacturing companies form the very foundation of the global economy....

This Is How Threat Actors Use OneDrive Compromise to Infect Local Windows Hosts
The trusted status of Microsoft cloud applications has inevitably resulted in...


EDR vs NDR: Why Endpoint Security Has a Clear Advantage
Choosing the right cybersecurity tools can be challenging in a crowded...
Investigation of an 8Base Ransomware Attack Uncovers Surprising Insights
Almost every engagement of the Eye Security Incident Response team provides new...