It all started with a phish
As part of our offer at Eye Security, we conduct regular phishing simulations for our customers to improve employee awareness. We are always looking to improve our services, we conduct a lot of research and development to ensure state-of-the-art technology continuously delivers the most value as possible for our customers.
With that in mind, we were testing out Microsoft's new ‘Attack Simulation’ offering (then called Attack Simulator) as a potential addition to our own phishing simulation program.
At first glance, their offer is a solid, basic phishing simulation program. A big benefit is the ease of payload delivery and complete integration with the Microsoft ecosystem. It means there is no need for whitelisting, which is necessary for phishing simulation campaigns that originate externally. Externally delivered campaigns can be a pain due to all the advanced phishing detection that takes place at Exchange Online.
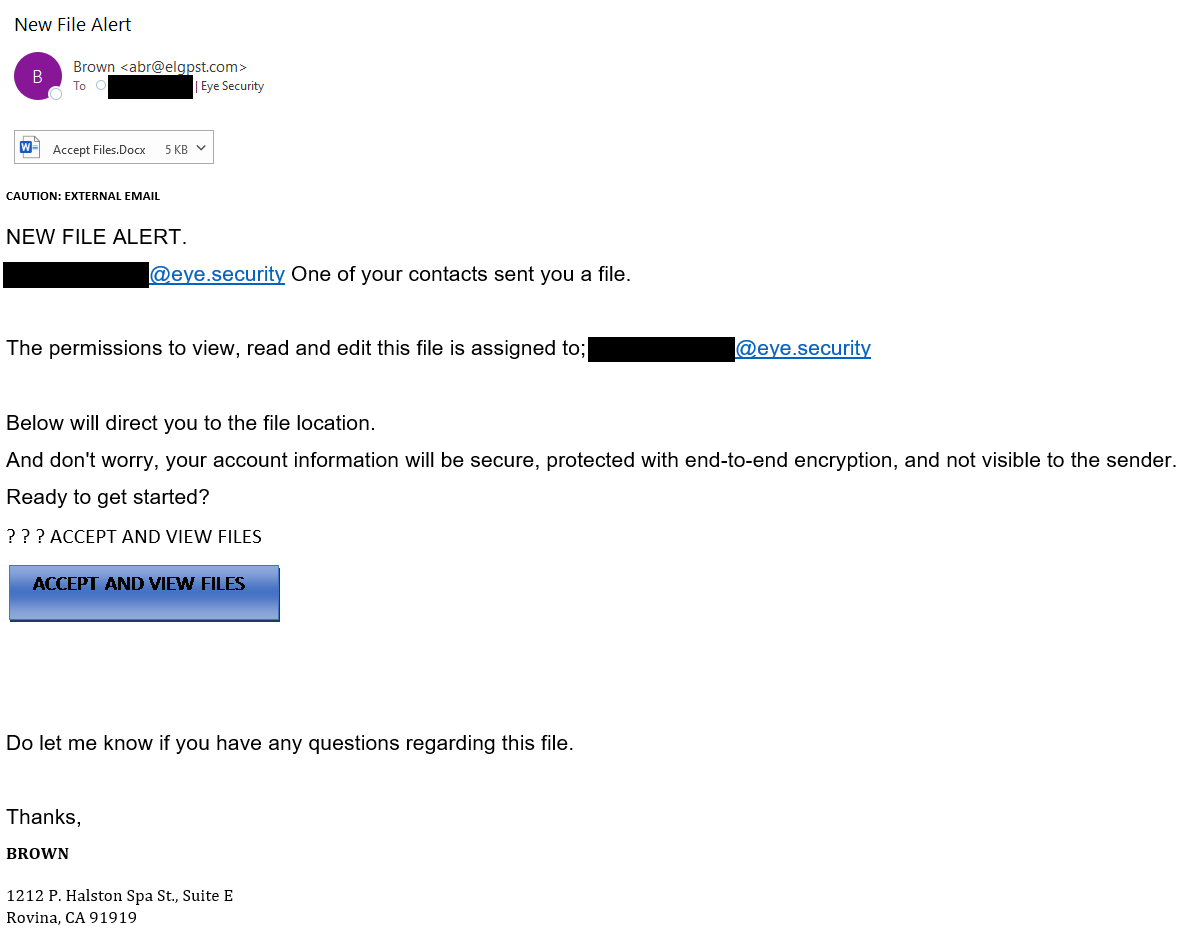
While the templates seem mediocre looking, with some cybersecurity professionals judging, "Nobody would click on that!", in my experience of sending phishing simulations to tens of thousands of people, yes, people do click on them. Here’s an example of one:
Master of every domain
Upon further review - and after sending myself a few templates and clicking around - I suddenly noticed something intriguing. One of the links used in the e-mail template pointed to a non-existing Confluence page. My curiosity got the better of me and I quickly registered the Atlassian account.
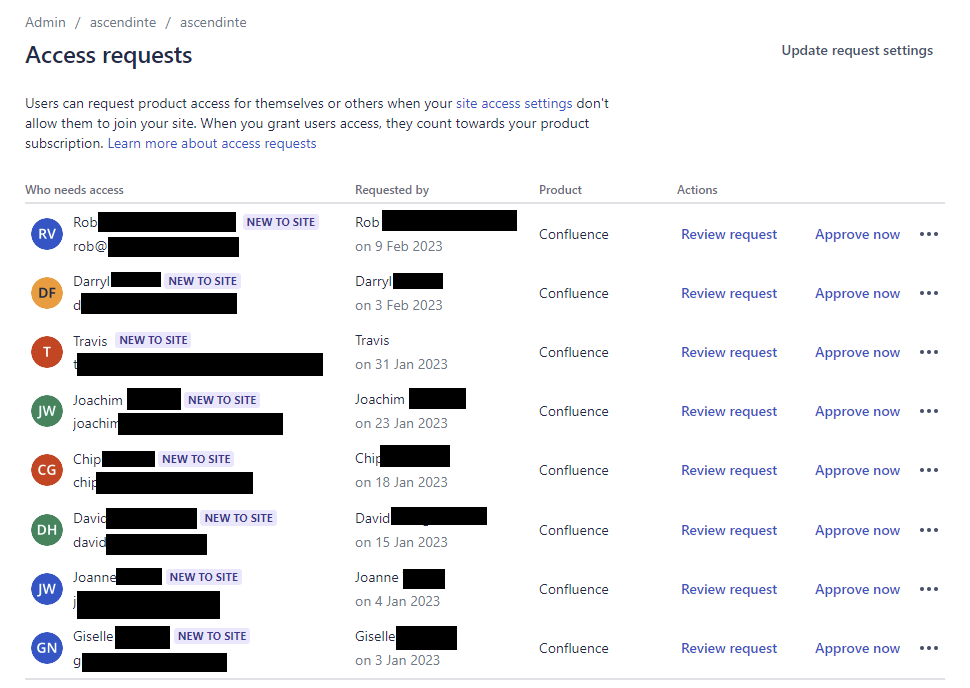
A few days later, almost forgetting that I registered it, I suddenly received an interesting e-mail.
People were starting to request access to my Atlassian page. That meant I wasn’t the only one ending up there. The template was being used by other users around the world who were targeted with Microsoft's Attack Simulator!
I investigated further and realised that the link not only pointed to a non-existing Confluence page, but the e-mail address used for sending the simulation was using a domain that was also not registered at the time. For $10 I registered the domain and after a couple of days, I started receiving replies to the simulation.
Emails from around the world
There were a range of responses. Some people were not fooled by the phish, but felt the need to reply anyway.
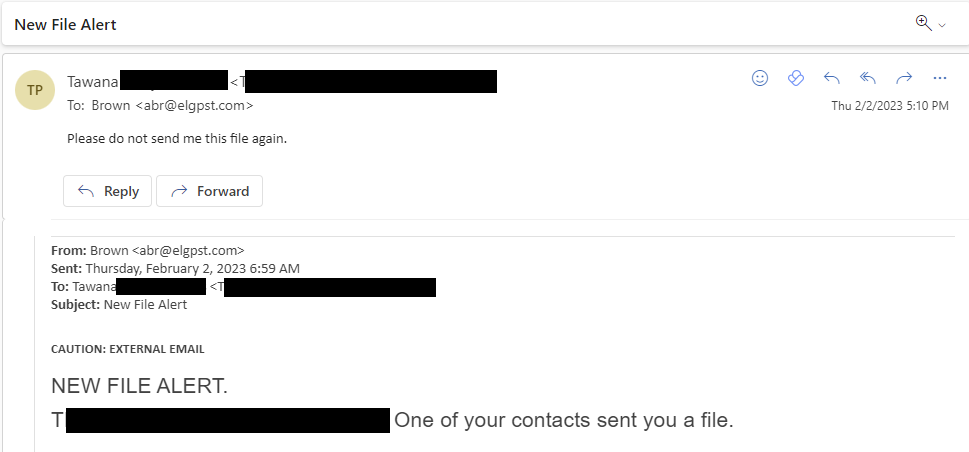
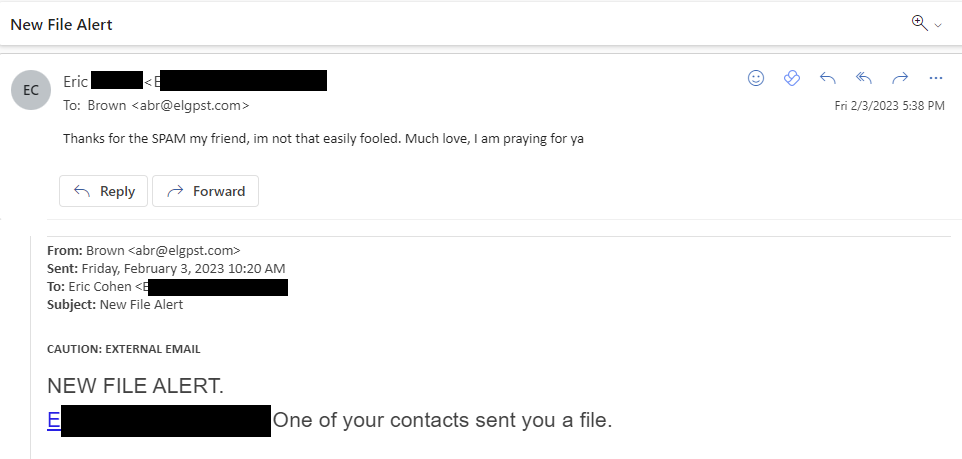
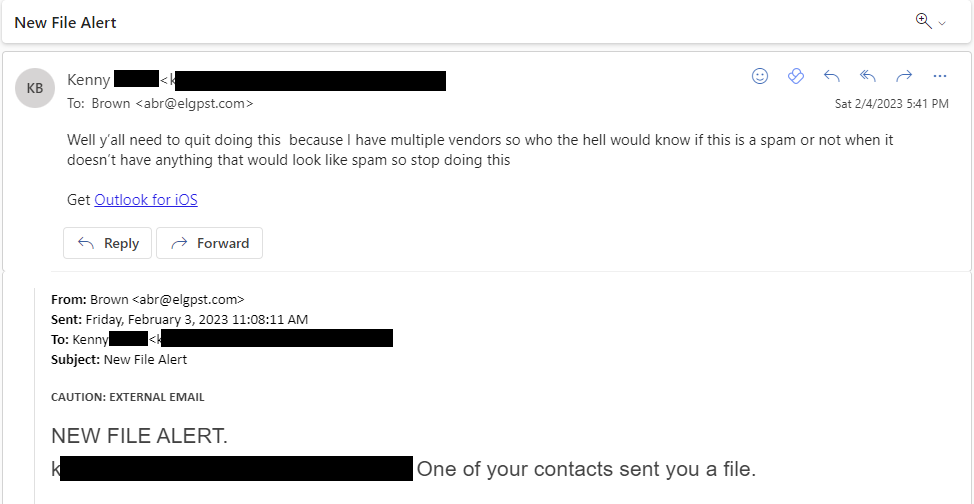
Others were on the fence. They might be convinced to open anything with a proper reply.
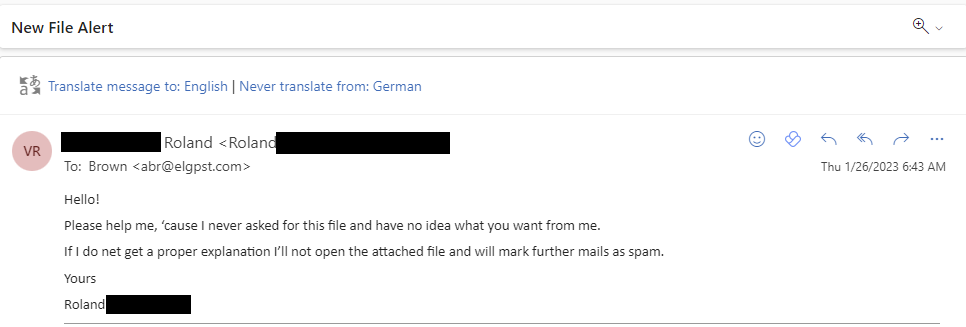
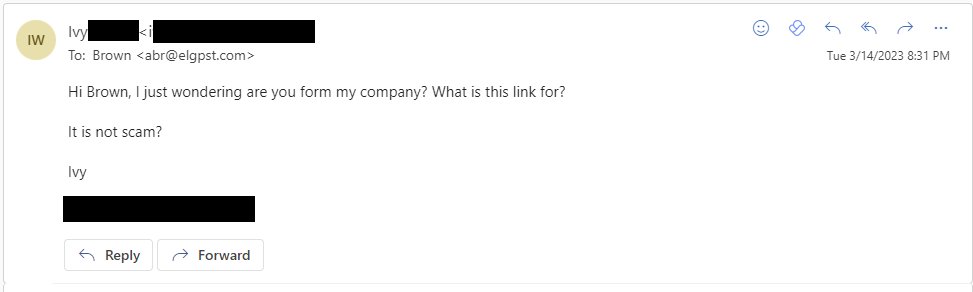
The majority though would do anything to receive a malicious attachment and open it. Even though they don’t know the sender or are working for a bank.
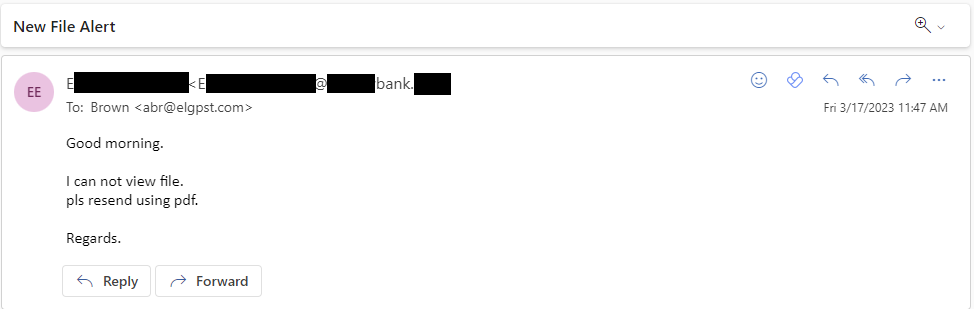
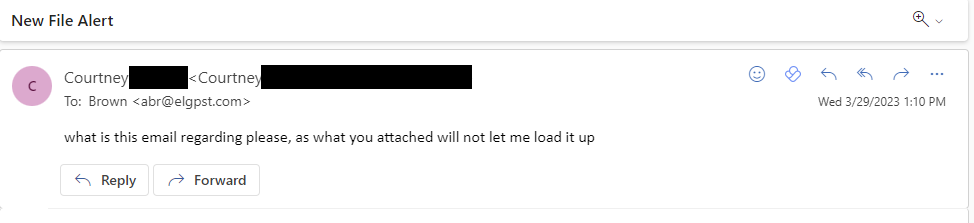
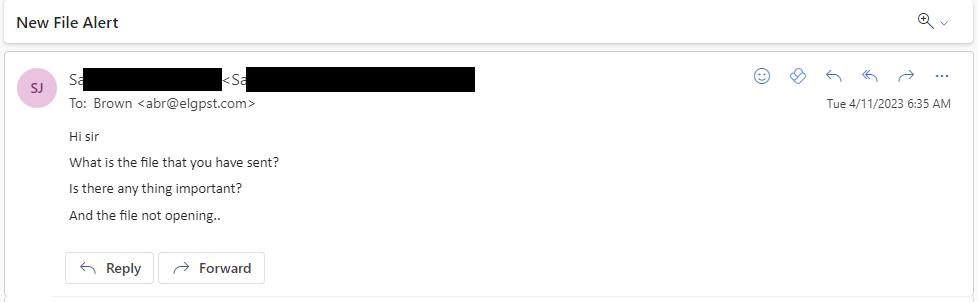
Collaborating with Microsoft
I quickly informed Microsoft about the security impact of this vulnerability. You can only imagine what a malicious actor would be able to do with this knowledge. If a malicious actor would have registered such a domain or Confluence page, they would have ended up with replies and visits by unwitting employees from companies around the world, all willing to click on suspicious links and access unsafe content.
Ironically, Microsoft’s Attack Simulator program would have turned into a real phishing attack platform that would have circumvented all protection mechanisms.
Microsoft was very quick in awarding a bug bounty, but it took them a while to come up with a fix. When I received the first notification that they fixed the issue, I realised that they only deleted a single template. Another report, another bug bounty and another long wait.
And so started a process of back and forth with Microsoft until they fixed the problem. Overall, my experience with the Microsoft Security Response Center (MSRC) has been very positive as they take all reports seriously and have a solid program in place to report and help fix any vulnerabilities.
Timeline
- January 23, 2023 - Reported the issue to Microsoft
- January 26, 2023 - Issue confirmed by Microsoft
- May 3, 2023 - Received a notification that the issue was fixed by Microsoft
- May 9, 2023 - Reported to Microsoft that the fix was incomplete
- May 19, 2023 - Issue confirmed again by Microsoft
- June 22, 2023 - Received another notification that the issue was fixed by Microsoft
- August 18, 2023 - Started writing this blog and noticed I still receive Access Requests on my Confluence page, reported again to Microsoft
- August 25, 2023 - Issue confirmed again by Microsoft
- October 2, 2023 - Received another notification that the issue was fixed by Microsoft
- October 10, 2023 - Noticed there were still some lingering links to external images, link titles, etc in some templates. Sent a final report to Microsoft
- November 2, 2023 - Final report marked as "moderate" and does not meet the bar for immediate servicing. Issue closed by Microsoft.
Conclusion
It goes to show preventative measures – such as awareness training, end point and cloud monitoring – are only the first line of defence. You need to assume that you will be breached so be ready to respond quickly.