Introduction
Battling cyber-crime can sometimes feel like an endless tennis rally where the cybercriminals relentlessly attack, and you are constantly defending, often just keeping the ball in play. But what if you could take the upper hand and have a chance at hitting back with a winning shot?
The current evolution of cyber threats demands innovative solutions to safeguard organisations. As cybercriminals continue to exploit vulnerabilities through various spoofing attacks, phishing attacks have seen an increase in both quantity and complexity. One particularly insidious form of credential phishing is Microsoft login page spoofing, which is itself an example of EvilProxy - a topic we discussed in an earlier article. A successful spoofing attack can lead to severe consequences such as data breaches and identity theft. But it goes further than just spoofing a page with an amateur UI. This technique copies and loads a pixel-perfect version of the page AND bypasses MFA, a man-in-the-middle approach that can result in a full-blown takeover of the victim’s account by the attacker. We’ve seen it emerge as a significant threat, prompting our dedicated team to develop a ground-breaking solution, aimed at fortifying your defences.
Understanding the rise of Login Spoofing and compromised login credentials
Phishing attacks have become increasingly sophisticated, preying on unsuspecting users who may unwittingly share sensitive information. Microsoft SSO is one of the most widely used, so a potent attack vector for malicious actors. Microsoft login page spoofing involves malicious actors creating deceptive, carbon-copy login pages, tricking users into sharing their credentials through fake login interfaces. These fake login pages closely mimic legitimate ones to capture sensitive information. Recognising the gravity of this growing threat, our team has crafted an innovative tool designed not only to detect such malicious attempts but also to empower users with visual cues that thwart phishing attacks in their tracks by preventing them from revealing their login credentials.
The inner workings of Eye Security against fake login page threats
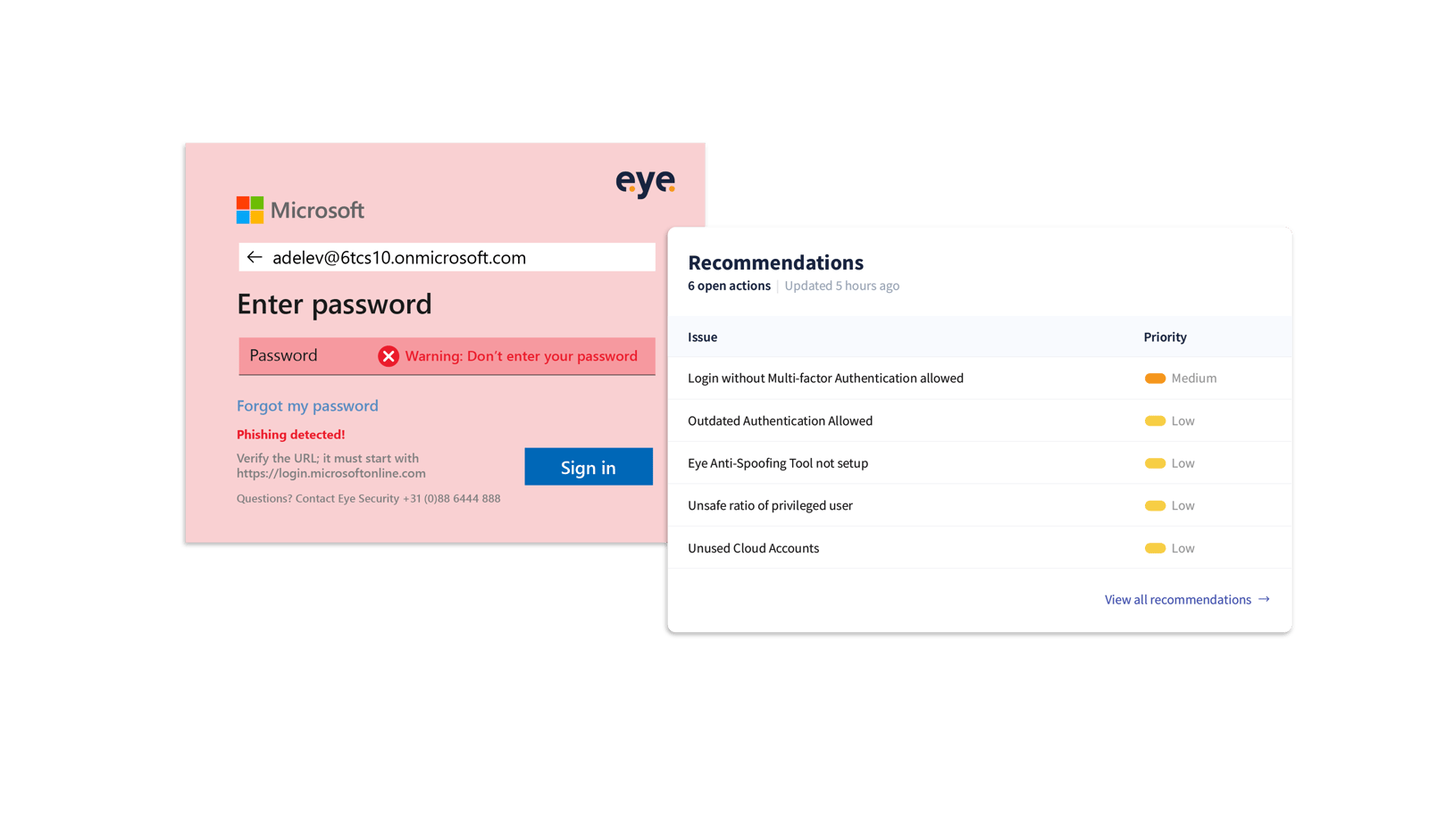
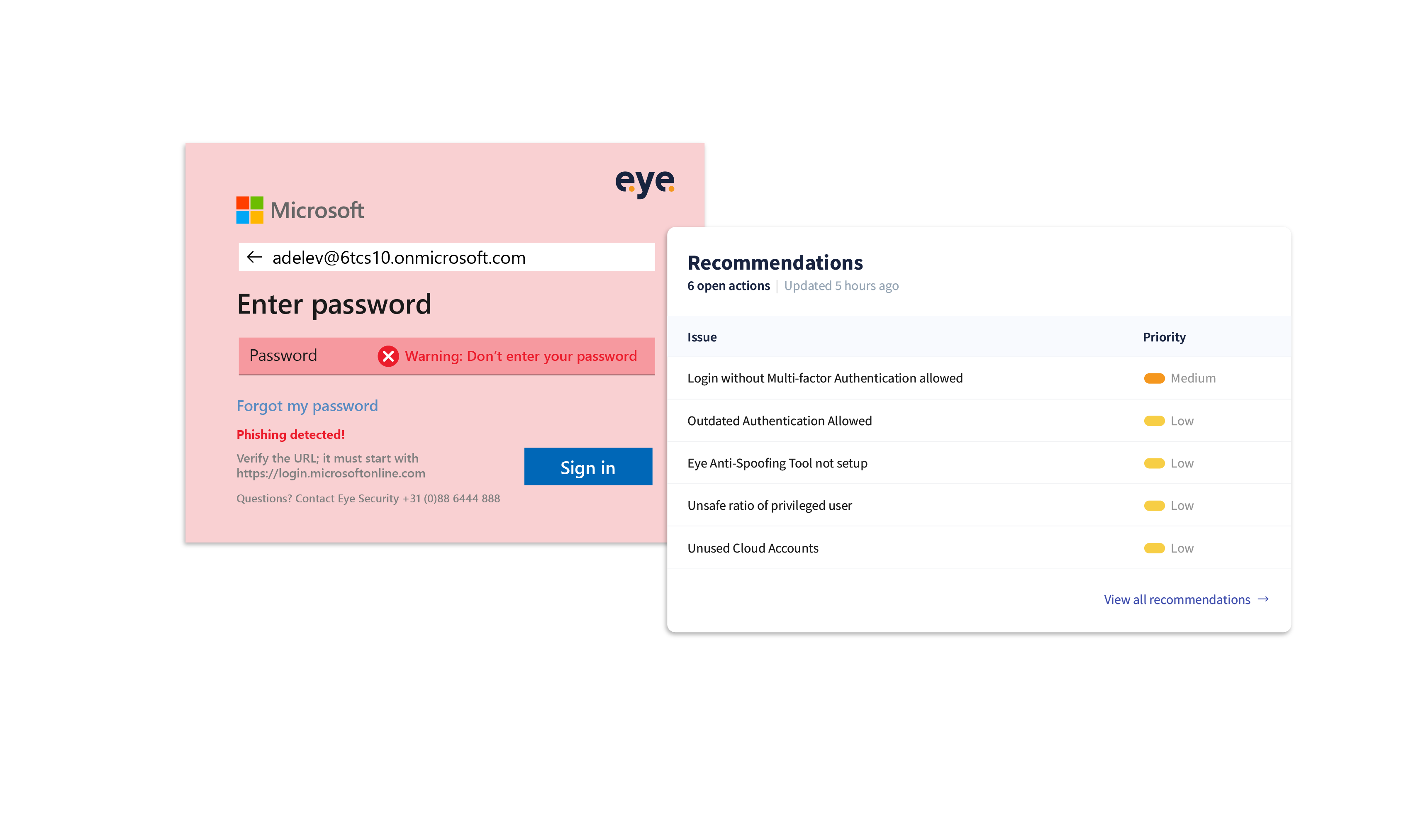
Eye Anti-Spoofing Tool (EAST) is our advanced cybersecurity solution, tailored to combat Microsoft login page spoofing. Spoofing attacks can bypass network access controls and compromise network security, allowing attackers to gain unauthorized access to sensitive data and systems. The tool operates during the sign-in process, employing a custom CSS file to customise the appearance of the sign-in box. Using a password manager can help identify potentially spoofed websites by autofilling login forms and recognizing trusted sites. As the user interacts with the login page, Eye Security’s servers dynamically adapt based on the HTTP Referer header, distinguishing between legitimate and spoofed websites, with our solution adding a visual clue. The custom CSS file will load a version of the login screen - hosted by Eye Security - containing a warning when the user is attempting to log in to an unrecognised domain. When the user accesses the legitimate Microsoft domain, a login page will load showing a green check box with the message: ‘login screen verified’. This ensures that users receive alerts if they encounter a credential phishing attempt, fortifying the security perimeter.
User alert mechanism for spoofing attacks
Imagine a scenario where an employee encounters a malicious phishing page disguised as a legitimate Microsoft login. Attackers often use a fake email address that mimics a legitimate source to deceive recipients. Thanks to Eye Security, users are promptly alerted after entering their username, but crucially, before entering their password. Visual cues, as shown in the screenshot below, serve as a warning, disrupting the phishing attack and preventing you or your colleagues from accidentally sharing sensitive information. Along with hundreds of other daily risk checks, you will also be notified in the Eye Portal, where you can see the recommendation.
A video we shared a few weeks ago demonstrated this in full. It was an iterative process, based on great ideas from Zolder BV. After researching their approach to generate insights into Adversary-in-the-Middle (#AitM) phishing kits and how to detect them, it was experimentation by our team of security experts that led to this new and innovative approach.
Since we launched EAST, several customers have already realised the value, most recently benefitting from the solution by preventing a business email compromise. In this case, the customer had got as far as entering their e-mail address, yet they chose not to type in their password on prompt thanks to the warning that EAST generates. Attackers look for human vulnerabilities to infiltrate systems, such as when you are filling in usernames and passwords on autopilot. That’s why you need cutting-edge solutions from specialists like Eye Security. Additionally, scrutinizing the sender's address in emails is crucial to detect spoofing attempts.
Domain spoofing is another tactic where cyber criminals manipulate website names to deceive users and advertisers, leading to ad fraud and phishing attacks. Tennis may be a one-on-one game, but inspiration from other players, and iterative collaboration within teams, leads to a better chance of winning.
Feel free to contact our support team for any help or questions you may have. Our customers’ security is our top priority and we’re here to support every step of the way.
FAQ
What is spoofing?
Spoofing is a type of cyber attack where an attacker pretends to be someone or something else to gain trust, access systems, steal data, or spread malware. These spoofing attacks can take many forms, including email spoofing, website spoofing, and IP spoofing. Cybercriminals use spoofing to trick victims into giving up personal information, clicking malicious links, or opening malware-laden attachments. Essentially, spoofing is a type of social engineering attack that preys on human vulnerabilities such as fear, naiveté, greed, and vanity. By understanding how spoofing works, you can better protect yourself and your organisation from these deceptive tactics.
What types of spoofing attacks are there?
There are several types of spoofing attacks, each with its own unique method of deception:
-
Email spoofing: his attack involves sending emails that appear to come from a legitimate source but are actually sent by an attacker. Email spoofing can trick victims into giving up sensitive information or clicking on malicious links, often leading to data breaches or malware infections. Attackers forge email header information to make their messages appear legitimate, tricking users into trusting the email and potentially exposing them to phishing or malware threats.
-
Website spoofing: In this type of attack, cybercriminals create a fake, spoofed website that closely mimics a legitimate one to deceive users into entering sensitive information. Website spoofing can deceive victims into entering their login credentials or downloading harmful software, compromising their personal or financial information. Malicious actors create deceptive, carbon-copy websites to capture sensitive information.
-
Caller ID spoofing: Manipulating caller ID information to deceive potential victims has become a common tactic whereby attackers disguise their phone number to appear as a trusted source. Caller ID spoofing is used by scammers to disguise their true identity and increase the likelihood of victims answering the call.
-
IP spoofing: This attack manipulates IP addresses to make it seem like traffic is coming from a trusted source. IP spoofing can be used to gain unauthorized access to systems or networks, allowing attackers to steal data or disrupt services. Cybercriminals send packets with a false IP address to gain unauthorized access to systems.
-
DNS spoofing: Also known as DNS cache poisoning, this attack involves altering DNS records to redirect traffic to a fraudulent website or server. DNS spoofing can lead to users unknowingly visiting malicious sites and exposing their sensitive information. Attackers corrupt the DNS cache to redirect users to malicious websites.
-
SMS spoofing: This attack involves sending text messages that appear to come from a legitimate source but are actually sent by an attacker. Text message spoofing can deceive victims into clicking on malicious links or providing personal information. Attackers disguise their identity to make messages appear from trusted sources, leading to phishing attempts and malware downloads.
-
Fraudulent sender address: Attackers forge email header information to make their messages appear legitimate, tricking users into trusting the email and potentially exposing them to phishing or malware threats.
- GPS spoofing: By manipulating GPS signals, attackers can make it appear as though a device is located somewhere it is not. GPS spoofing can disrupt navigation systems or trick victims into revealing sensitive information based on their perceived location.
- ARP spoofing: This attack manipulates ARP messages to associate an attacker’s MAC address with a legitimate IP address. ARP spoofing can enable attackers to intercept, modify, or block data intended for other devices on a network.
How to prevent spoofing attacks?
Preventing spoofing attacks requires a combination of technical and non-technical measures. Here are some steps you can take to protect yourself and your organisation:
-
Use strong passwords and enable two-factor authentication: Strong, unique passwords and two-factor authentication can prevent unauthorised access to your accounts and systems.
-
Keep software and systems up to date: Regularly updating your software and systems with the latest security patches can help prevent exploitation of known vulnerabilities.
-
Use antivirus software and a firewall: These tools can detect and block malware and other online threats, providing an additional layer of security.
-
Be cautious of suspicious emails and websites: Always scrutinise emails and websites before providing sensitive information or clicking on links. Look for signs of spoofing, such as unusual sender addresses or URLs.
-
Use a spam filter: A good spam filter can block most spoofed emails from reaching your inbox, reducing the risk of falling victim to email spoofing.
-
Log in through separate tabs or windows: When accessing your accounts, use a separate tab or window to avoid phishing attacks that may be embedded in other web pages.
-
Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic, making it harder for attackers to intercept and manipulate your data.
-
Educate yourself and others: Awareness is key. Educate yourself and your colleagues about the risks of spoofing attacks and how to recognise and prevent them.
By implementing these measures, you can significantly reduce the risk of falling victim to spoofing attacks and protect your sensitive information from cybercriminals.
-